Introduction
This post will help you to have a quick start as well as deep understandings of the mechanism behind some basic features of Azure networking.
This post is especially fit for those who are already familiar with AWS VPC and now starting with Azure Vnet.
The contents of this post are:
- Compare Azure Vnet and AWS VPC.
- Fundamental and essential keys to work with Azure vnet.
1. Azure Vnet vs AWS VPC
| Feature | Azure Vnet | AWS VPC |
|---|---|---|
| Subnet AZ | 1 subnet can spread over multiple AZ. | 1 subnet can only be in one AZ. |
| Internet Gateway | Azure dose not have an entity called Internet GW, however, if you are from AWS, we can say the Internet GW is attached by default, can not be removed. | Not attached by default, attach/remove by users. |
| NAT GW | Default NAT-GW is attached, can not remove the default NAT-GW. Users can attach/remove a custom NAT-GW | Not attached by default, attach/remove by users. |
| Security | Security Group, Firewall | Security Group, NACL, Network Firewall |
| Bastion host | PaaS Bastion host: Serverless, fully self-managed | IaaS Bastion host: Use an EC2 with public IP, users have to configure all the routing/security policies needed. |
2. Azure Networking
2.1 Subnet
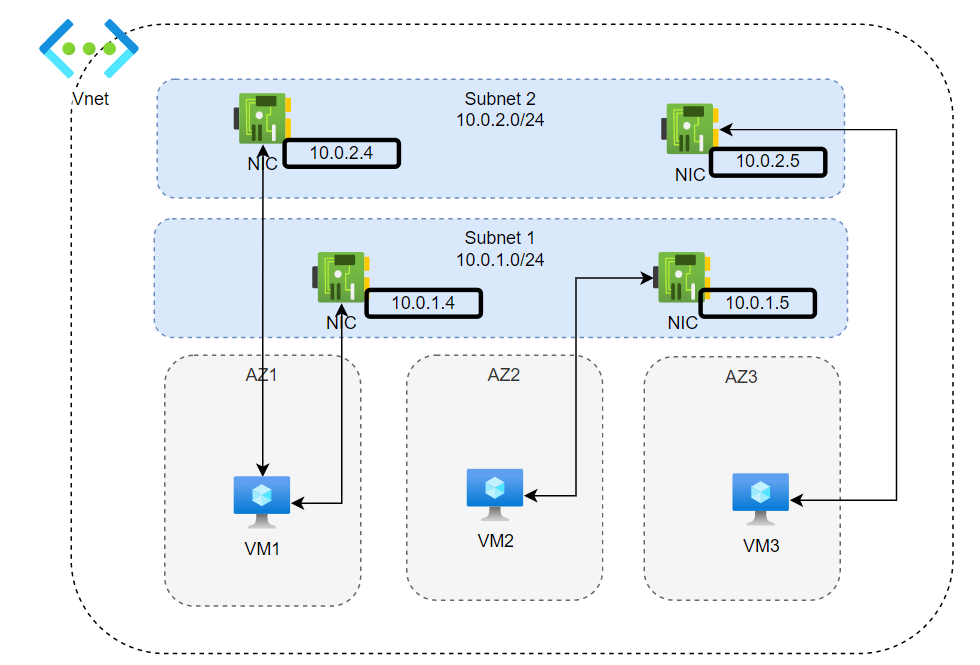
- There is no AZ boundary for a subnet in Azure Vnet.
- A VM belongs to an AZ (VM and subnet are independent).
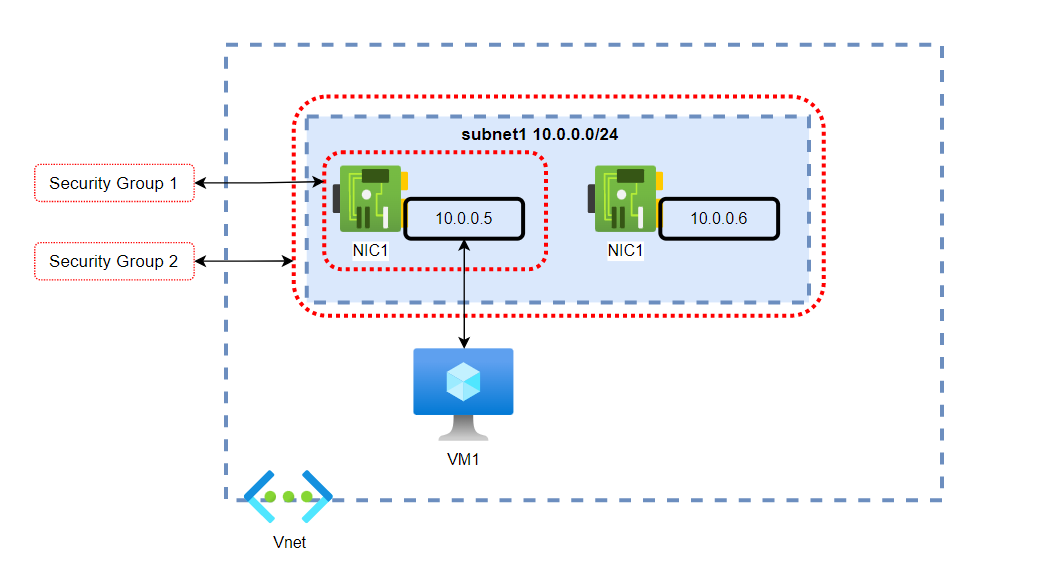
- A NIC belongs to a subnet.
- One VM can have one or multiple NIC attached to it depending on the VM size.
2.2 NIC, Internet GW, NAT GW.
-
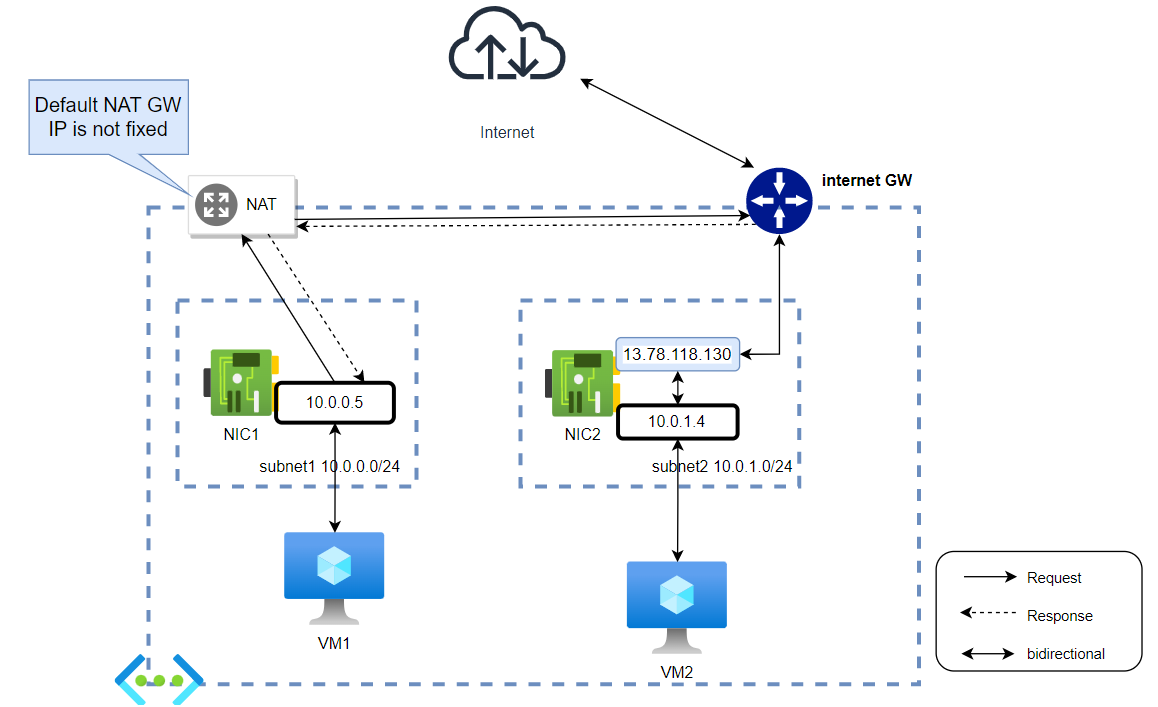
By default, each Vnet has an Internet GW and a NAT GW attached to it. (Unlike AWS, in Azure Vnet, they don’t really have the definition for Internet GW, I just put it there for better imagination, especially for those who came from AWS). We can not detach these default GW from the Vnet. So by default, all VM can already access to the Internet without any NAT, routing configuration.
-
VM with only private IP can reach the Internet via NAT GW, VM with Public IP will reach the internet via the Public IP.
-
NOTE, the public IP is actually not attached to the VM directly. if we try "ifconfig" on the VM, only the private IP is shown. When the VM goes to the internet, it goes through the private IP first, then NAT to its Public IP.

-
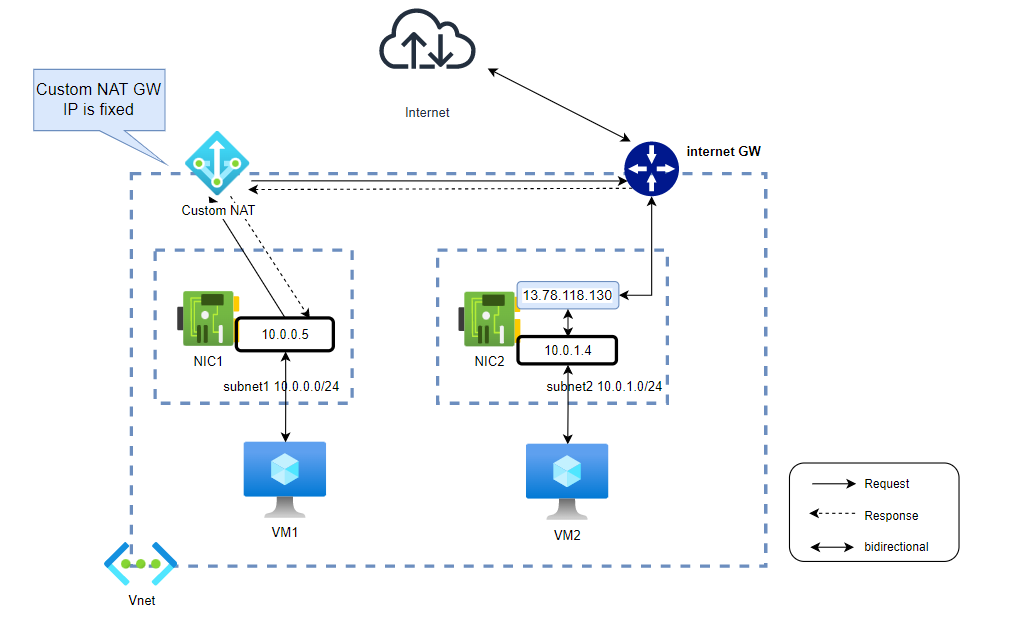
Custom NAT GW
With the default NAT GW, its public IP is not static. If you need a Public static IP for your NAT, deploy a custom NAT GW.

2.3 Network security group
- A security group has inbound and outbound rules lists. There are 3 default inbound rules and 3 default outbound rules, you can not remove or edit them.
- You can add/edit/remove your custom inbound rules, outbound rules. Each rule has a "Priority" number, the rule that has a smaller "Priority" number will have a higher priority (sounds funny, but it is).
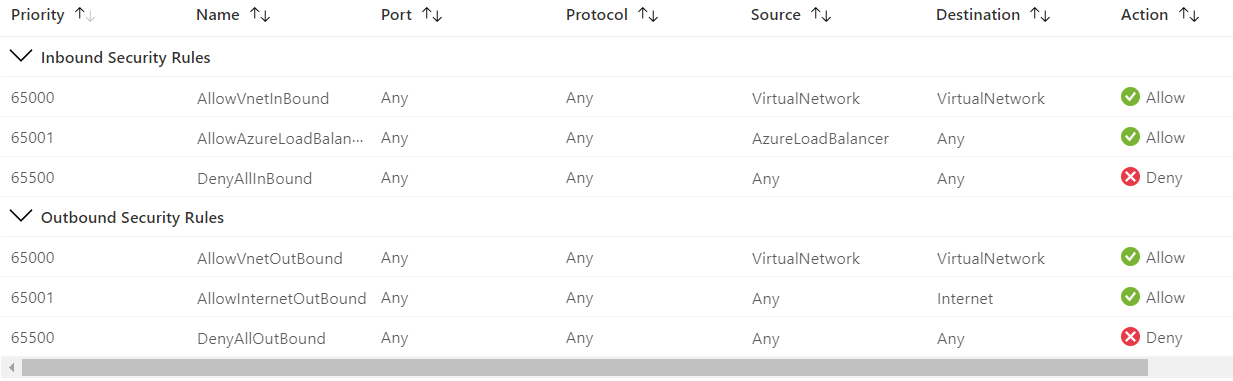
- Security groups can be attached to NICs or subnets.










Vui lòng đăng nhập để bình luận.